In Part 1 of this series, we discussed the fundamentals of ISO 27001 compliance – specifically, the growing demand among international companies to make their vendors ISO compliant to align with the European General Data Protection Regulation (GDPR).
In this part, we will explore the steps needed to implement an Information Security Management System (ISMS).
What are the six steps to implement an Information Security Management System (ISMS)?
Here are the six steps to implement an Information Security Management System (ISMS)
- Scope the ISMS
- Asses Risk
- Respond to Risk
- Implement Controls
- Perform Internal Audits
- Ensure Continous Improvement
The ISO 27001 document contains a high-level summary of the steps to build, maintain, and optimize an ISMS. Each step provides a flexible, risk-based approach to security. As ISO documents can sometimes be dense, we have condensed the concepts into Six Steps.
1. Scope the ISMS
Before you can implement an ISMS, you must first define it. You may notice that this step has a lot in common with classic risk management practices.
The scope of an ISMS includes:
- Information Assets: A generic term that refers to anything in-scope – data, computers, networks, applications, and so forth. Developing a comprehensive inventory of information assets is often an overlooked step in many security programs, yet is critical to building an ISMS.
- Asset Value: A valuation of those assets. This is not a dollar value, per se, but how important the asset is to the business. For example, a single iPad may have a low value, but your customer database would have a huge value.
- Information Technology Requirements: Any business requirement that drives the need to use a particular technology, application, or configuration. For example, if your company must use Oracle software because of compatibility with a business process, then you must define that requirement.
- Contractual Agreements: This includes any legal, regulatory, or vendor relationships that impact information assets. For example, if you host some of the assets in AWS, then your agreements with AWS would be in scope for ISO compliance (which is good, because AWS has a robust compliance program!)
2. Assess the Risk
After scoping, you must assess risk on the in-scope assets. But before you can assess risk, you must first define the risk assessment methodology you use. The ISO 27005 document provides a guideline on how to conduct a risk assessment, but you are not required to use that approach. At Anitian we use our exclusive RiskNow® approach, which is an optimized and accelerated version of NIST 800-30 and is fully aligned with ISO 27001.
At the most basic level, a risk assessment must:
- Establish an inventory of threats the in-scope assets face
- Attribute vulnerabilities to those threats
- Attach a probability and impact of each threat, based upon the controls in place
- Determine the amount of risk present
- Define improvements that would reduce risk
- Define the residual risk if the improvements were implemented
Ultimately, a risk assessment is all about feeding you and your leadership intelligence so you can make informed decisions about the risk you face, and how you will respond to that risk.
The risk assessment is an iterative process. However, the first assessment is critical since it will shape the controls implemented to mitigate threats.
3. Respond to Risk
After completing the risk assessment, the next step is to determine how you will respond to the identified threats. There are three possible responses: accept, mitigate, or transfer.
You must not only decide what to do with each threat, but also justify that treatment. If you implement controls to mitigate a threat, you must define what those controls will be and how they will effectively mitigate the threat. If you intend to transfer the risk to another party, you must define how the third party will assume the risk. If you are going to accept the risk, then you must provide a rationale for that.
4. Implement Controls
After you have determined how you will address each of the threats identified in your risk assessment, you must then select and implement the security controls needed for risk mitigation. Many consider this the most crucial, and therefore the most contentious, part of ISO compliance.
There are two categories of security controls ISO addresses: administrative and technical.
- Administrative controls include policies, procedures, and guidelines
- Technical controls are all those “fun” things like firewalls, event logs, encryption, and anti-malware
ISO 27002 provides a reliable control set that aligns with general best practices. However, like the risk assessment guidelines, this control set is not mandatory. You are free to choose what controls your business needs.
ISO 27001 requires you to take a risk-based approach to control selection. That is the purpose of the risk assessment in Step 3. You must identify what threats and vulnerabilities you have, determine the risk they present to your company, and then select controls that mitigate any threats you do not choose to transfer or accept.
While the ISO 27002 control set is a sound baseline, if you are also complying with other standards such as PCI, NIST 800-53, or SOC2, then you should start by mapping your current control set to ISO 27002 to identify what is already in place.
When selecting ISO 27001 controls, be sure that you document your rationale. A common mistake people make is to focus on the selection of a technology vendor, not the control itself. The brand of firewall or SIEM you choose is ultimately not relevant to ISO compliance. Rather, you must document the control’s purpose, how it will be deployed, and what benefits it will provide toward reducing risk. This is critical when you undergo an ISO audit. You are not going to pass an ISO audit because you picked an NGFW that is in the “good” Magic Quadrant.
We will talk more about ISO audits in Part 3 of this blog series.
Furthermore, be cautious about selecting any product that promises “guaranteed compliance” (the infamous “compliance appliance”). There is no such thing as an “ISO-compliant” product (this applies equally to PCI, NIST, SOC2, etc.).
5. Perform Internal Audits
With your security controls selected and deployed, you must now ensure that these controls are maintained. Step five is all about developing an internal audit program to verify the effectiveness of your ISMS.
This is best achieved through making compliance a “business-as-usual” practice. Any compliance effort causes organizational change. In our experience, forcing this change on people is rarely effective. It is more effective to incentivize people to naturally adopt security controls through a strong Security Vision, resulting in a Culture of Security.
Security Vision begins with leadership routinely promoting and evangelizing good security. When leadership supports security, employees will naturally follow, and proactively seek to maintain a Culture of Security. Failure to do so results in contention from control owners, rather than buy-in. However, while a Security Vision may ensure that controls are followed, you will still need a formal validation of the effectiveness of the ISMS.
ISO 27001 clause 9.2 defines some of the aspects of a formal internal audit program. The key takeaway is that you must define how you will assess internal controls as well as the criteria you will use to determine if they are effective or not.
Many organizations outsource the testing of controls to provide independent assessment and feedback. However, there is no requirement to use outside personnel. As long as you define an audit process and criteria, and then follow that process, you will meet ISO requirements.
6. Ensure Continuous Improvement
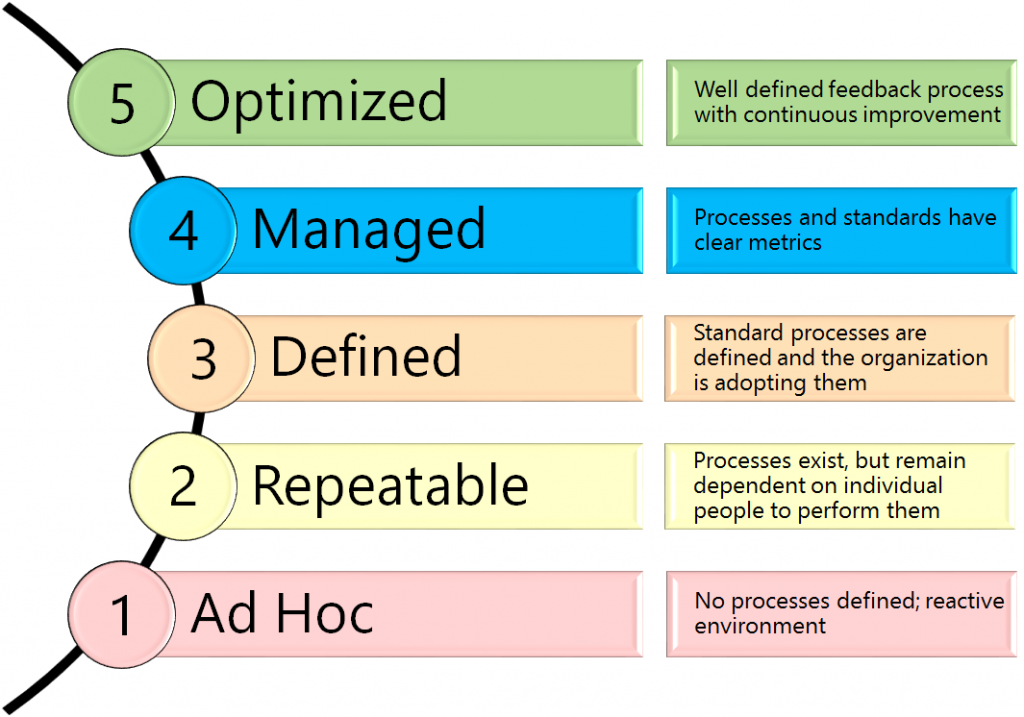
The final stage of ISO compliance is to implement a feedback mechanism to provide continuous improvement for the entire ISMS. The most common approach to achieve this requirement is to adopt a maturity model for all the controls.
Maturity models rank control effectiveness. The classic maturity scale, shown below, ranks controls on a five-point scale. The intent is for each control to be assessed and ranked based on how effective it is and how well it is managed. The ideal state is for all controls to have well-defined standards, policies, and procedures coupled with a process to assess and improve them regularly.
This is another part of ISO 27001 compliance where an outsourced vendor can help. Most security testing firms will not only test the effectiveness of a control but can also provide recommendations for improving those controls. Furthermore, in our experience, the assessment and recommendations of an external vendor tend to meet with less resistance from internal staff.
Stay Tuned
Join us tomorrow as we wrap up the ISO 2700x journey with a discussion of the ISO audit process.



2 thoughts on “ISO 27001 – Part Two – Building an ISMS”